Cloud Security In A Nutshell
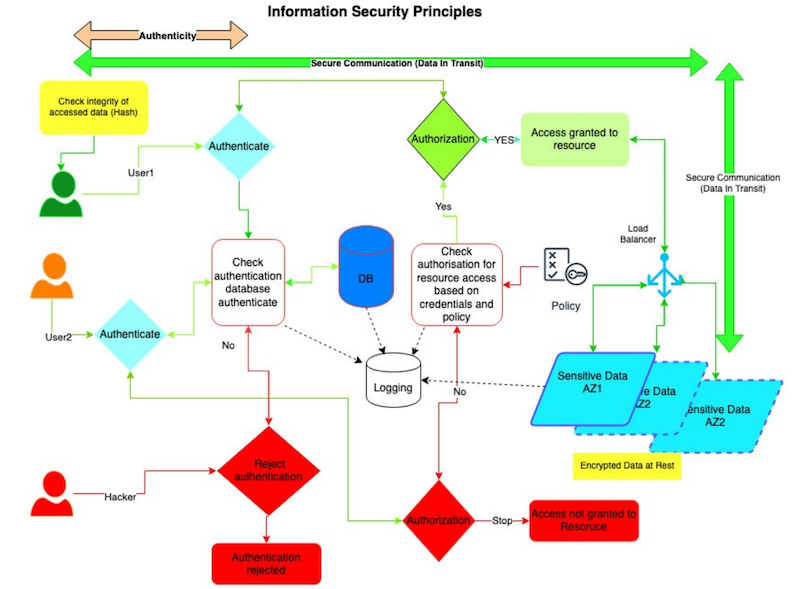
Security Principles: CIA TRIAD, Accountability, Authenticity and Risk:
Whether it be the cloud or data stored on your computer security principals remain the same, they are as follows:

Confidentiality
Confidentiality ensures that sensitive information is available to only those who are authorised to access access it. Secure all data in transit and rest. (Authorization of access to data should be based on the least privilege model, which means that access to data should be given only as required. If an organisation has ten data sets and you are authroized to access only two of those, you should be given access to only those two data sets to fulfill your task).
Integrity
Integrity ensures that data is not altered by unauthorised entities. (Ex: Test checksum of data). Ensure non tampering of data.
Availability
Availability ensures that data is available to authorised users whenever and wherever they require it. Availability needs to be architected when designing a system. (Ex: Resources Load balanced across multiple availability zones or data centers to ensure avaliabiltiy requirements of the organisation.
Non-Repudiation
Non-repudiation is achieved through cryptographic methods which prevents a person or entity from denying having performed a particular action related to data for proof of obligation, intent, or commitment; or for proof of ownership.
(Legal proof).
Authenticity
Authenticity is the assurance that the data, transactions, communications or documents (electronic or physical) are genuine. It is also important for authenticity to confirm that both parties involved are who they claim they are. Authenticity enhances integrity.
Risk Assessment
The business requirements of an organisation will help to derive risk weight of an asset within the organisation to enable the application of security controls to protect its data based on the security principles. The business legal obligations such as PCI, GDPR, HIPAA, NIST 800-63 standards based compliance requirements has a major impact on the security controls required to be implemented.
The following graphic decribes the above principals in action (Other than Risk Assessment) when data is hosted in a cloud environment.
Cloud Security Shared Responsibility Model
The shared responsibility model depicts the sharing of security responsibilities when hosting data in public cloud environments between the (CSP) cloud service provider and the customer. The cloud service provider is responsible for the security “of“ the cloud while the customer is responsible for the security of data hosted “in” the cloud.
Though the services and the underlying architecture provided by different cloud providers maybe diverse and maybe named differently the following shared security model diagram published by AWS can be applicable to other cloud service providers as well.
https://aws.amazon.com/
compliance/shared-responsibility-model/

Enhancing Security of Existing Cloud Architecture
Enhancing security within an organisation can be complex, we can work with you to implement the following security measures and much more.
Utilise hardware tokens, push notifications, SMART cards for high security applications. Utilise FIDO (asymmetric key authentication standards).
Standardise IoT security (IoT ASVS).
Security automation and testing during every CI/CD release cycle of IAC code and application code.
Always utilise the security by design principle when deploying workloads into the cloud.
Landing zones in cloud.
Core Accounts
Organisational Account:( Account Vending/ IAM account(SSO).
KMS account:(Customer Master Keys).
Security Master Account: (All security feed into this account, for auditing etc, centralised view of security within organisations).
Shared service account (AD, etc).
Logging Account (CloudTrail (Organisational Cloud Trail), Stream CloudWatch Logs to S3 to the centralised account.
(Cloud Trail, CloudWatch Logs:VPC Flow Logs, DNS Query Logs, Instance Logs via agent).
Send CloudTrail Events to CloudWatch Logs.
Utilise means to send logs to a centralised account (Kinesis Firehose> Lambda>S3).
Search Data for quick response S3> Lambda> ElasticSearch.
Utilise a centralised Dashboard, Kibana DashBoards.
Optional splunk can be utilised for logging.
Automated or manual response to events : Logs>Events>Response.
Child accounts deployed and configured via StackSets to apply security baselines and security policies.
CI/CD Pipelines security based (Account Deployment, Apply account Security baselines to child accounts).
AWS Tools
Service Control Policies, AWS Config Rules.
AWS Security Hub aggregates, organizes, and prioritizes your security alerts from Amazon GuardDuty, Amazon Inspector, Amazon Macie, AWS Identity and Access Management (IAM) Access Analyzer, and AWS Firewall Manager, as well as from AWS Partner solutions.
Incident Response. Preparation>Identification>
Containment>
Investigations>Eradication>
Recovery>Follow-Up (Automated play books).
Utilise securely configured service catalogues (Reusable secure blueprints) (AWS Service catalogues).
Reduce blast radius (SOA Oriented Architecture, Organisation, limit accounts with SCPs, different VPC).
Monitoring and alerting and remediation.
S3> CloudTrail>CloudWatch Logs>CloudWatch Metric Filter>CloudWatch Alarms>SNS Topic>Alerting>(Lambda/SSM)
Third Party tools (Data Dog, Palo Alto, Alert Logic, Sumo Logic,Dome9).
Threat signature detection engines (Antivirus, WAFs etc: Malware, DDoS distributed denial of service, SQL injection, phishing(email), XSS cross-site-scripting, zero-day, MitM man in the middle, business logic, defacement attack mitigation).
Key Management (Key Creation, Rotation, Storing, Securing Keys) (Symmetric/ Asymmetric, Cryptography, Access key rotation).
Application security is fundamental to all security (Mitigate against SQL injections etc, parameterization) (API Gateway).
Deployment of infrastructure as “code” (immutable infrastructure). (CloudFormation, Ansible,Terraform).
Test architecture for failure, service availability and vulnerabilities. (Disrupt services and exploit vulnerabilities in a controlled environment :Chaos engineering).
Utilise IDS/IPS, WAFs (Palo Alto, Alert Logic, AWS WAF etc).
Data Classification (Resource Tagging). (AWS Macie).
Refer to and understand CVE’s for types of workloads. (Common Vulnerability Exposures).
Identity and access management (Principle of Least privilege, SSO, RBAC role based access, 2FA, facial recognition and thumbprint).
Utilise detective Controls( Rule engines Lambdas, AWS Config etc). (Example change S3 security revert back via lambda).
Protection of data at rest and in transit. (Client/Server side encryption, Secure communication (HTTPs)). (KMS, AWS Certificate Manager).
SOC (External & internal scanning services). (External scans OWASP top 10, internal scanning of all other vulnerabilities CWE).
VPC (Peering, Endpoints, Transit-Gateway (internal routing)). (Ensure traffic is local to the service provider data centers where possible).
Regularly audit account access. (IAM Analyser).
Never forget basic housekeeping.
Regularly check SSL certs for unexpected certs.
Penetration testing, patching and hardening of images and applications. Utilise CIS hardened images when possible. (AMIs).
Utilise a Password Manager (Instead of slack).
Secure LDAP.
Use company based email accounts when deploying services.
Data redaction in WAFs (where the data is decrypted at the WAF layer utilising the private key for security monitoring).
Keep TLS versions upto-date.
Test security updates or any changes in a test environment first.
Document security and operational procedures and train staff to adhere to these security and operational procedures.
Disable unused services and regions within the cloud environment.
Be agile utilise change control to update resources and services regularly via delta periodic changes instead of doing massive changes at infrequently.
Test security of these changes continuously through security automation.
Secure DNS (cloud-based, authoritative DNS services that uses DNSSEC, Asymmetric Encryption, validation chain for Zone Data).
Attacks (DoS, Cache Poisoning, False Authoritative Servers, Modified Zone Data) .
Zone data is publicly signed.
Enable DNSSEC validation on all recursive servers.
DNSSEC sign all zones.
Utilize registry/registrar locking for all critical zones.

Types of attacks and vulnerability areas to focus on
Artificial intelligence attacks (Deep Fakes, thumbprint and face/voice recognition vulnerabilities). Hackers may outpace patch updates, weak serverless architecture code can be compromised, misconfigured insecure third party services can be compromised, vulnerabilities in microservices (containers), password & SMS authentication mechanisms, misconfigured cloud services (IAM, Keys, S3 etc). Cloud DDos attacks,
unskilled attackers accessing vulnerabilities in IoT devices ( Firmware/OS not being secure), too many isolated security tools, machine learning vulnerabilities, vulnerabilities in CI/CD pipelines, Cloud DDoS vulnerabilities, digital transaction vulnerabilities, application vulnerabilities.
Possible forward thinking and valuable solutions:
Centralised single pane view of all security within an organisation.
Train security staff, technical, non technical staff and customers. (Application developers utilise ASVS standard). Ensure security staff are competent.
Threat modeling responsible disclosure vs full disclosure. (Minimise impact to the public, giving deadlines to the party involved). frameworks :STRIDE, Cyber Kill Chain) Tools: OWASP Threat Dragon, Tutamantic (Design and architecture phase), PyTM (Check code), IriusRisk (Enterprise, Cloud).
Utilisation of tools that that have security baseline standards that are built into them (Palo Alto Prisma, Dome9, Darktrace).
Harden environment by utilising tools and tactical procedures that adversaries use.(Have War Games, bug bounty etc, within the organisation).
Security measures being reactive than proactive. (Focus on tools procedures and attack methods, rather than compliance tick boxes).
Threat model CI/CD Pipelines.
Behavioural analytics of SAS and Cloud applications, anomaly detection (real time log analysis, alerting, threat detection, machine learning to analyse behaviours of the application at all layers).
Alerts and responses based on behaviour of an entity, unusual behaviours of an application is alerted for immediate security responses. False positives are learnt through machine learning and our not triggered once a behaviour is accepted. (Amazon Guard Duty).
Filtering alerts in multiple stages (Pyramid structure) through machine learning and security algorithms to reduce false positives.
SOAR, Security orchestration automation and response tools: (SOC analysts can become more efficient when utilising SOAR tools, helps in threat monitoring and response, threat investigation and response, and threat intelligence management).
Threat intelligence systems: Aggregation of alerts and threats, risk scoring systems, reduction of false positives).
Normalization - Consolidating data across different sources formats.
De-Duplication - Removal of duplicate information.
Enrichment - Removal of false positives, scoring of indicators, and the addition of context.
Application of threat intelligence and security analytics at all layers of a service, (the service provider the end users and of the application).
Audit cloud environments regularly and periodically utilize third parties and native cloud security tools.
Cloud DDos mitigation services. (CloudFlare, Neustar,Nexusguard etc,) .
Block Chain, (Smart contracts, replicated distributed objects, be aware of the 51% attack).
Blockchain can determine if a file has been tampered with, provide information about where and when the tampering occurred. Helps to maintain a chain of custody and ensuring that data has not been manipulated. (Decentralised trustless, Immutable,consensus proof of work, utilises certificates instead of passwords, secures data with cryptography properties hashing and digital signatures).
